MEDIATECH
Bridging The Gap
Vernon Taylor Enterprise Alliance (VTEA) and
Media Split Encryption™ products
VTEA and Media Tech join forces to address the critical issue of data security. Securing data poses several significant challenges. With the increasing sophistication of cyberattacks, data breaches are a constant threat. Attackers may exploit vulnerabilities in systems to gain unauthorized access to sensitive data. Malicious or negligent actions by insiders, such as employees or contractors, can jeopardize data security. This includes intentional data theft, accidental data exposure, or misuse of privileges.

While encryption helps protect data from unauthorized access, managing encryption keys securely and ensuring proper implementation can be challenging. Weak encryption algorithms or improper key management can compromise data security. Data loss can occur due to various reasons, including hardware failures, software bugs, or human error. Implementing robust backup and recovery processes is essential to mitigate the impact of data loss incidents.
Organizations must comply with various data protection regulations, such as GDPR, HIPAA, or PCI DSS, depending on the type of data they handle. Achieving and maintaining compliance can be complex and resource intensive. With the adoption of cloud computing, securing data stored in cloud environments is critical. Organizations need to address concerns such as data confidentiality, integrity, and availability when using cloud services.
The proliferation of mobile devices introduces additional challenges for data security. Securing data on mobile devices, managing access controls, and protecting against mobile-specific threats are essential considerations. Establishing clear policies and procedures for data access, usage, and sharing is essential for maintaining data security. Effective data governance ensures that data is handled in a secure and compliant manner across the organization.
Rapid advancements in technology, such as artificial intelligence, IoT, and blockchain, introduce new security risks and challenges. Securing data in these emerging environments requires ongoing vigilance and adaptation.
There is a shortage of skilled cybersecurity professionals, making it challenging for organizations to build and maintain robust data security capabilities. Investing in training and talent development is crucial to addressing this challenge.
Addressing these challenges requires a comprehensive approach that combines technical controls, security best practices, and ongoing risk management efforts. Organizations must continuously evaluate and improve their data security posture to adapt to evolving threats and regulatory requirements.
Products and Sevices

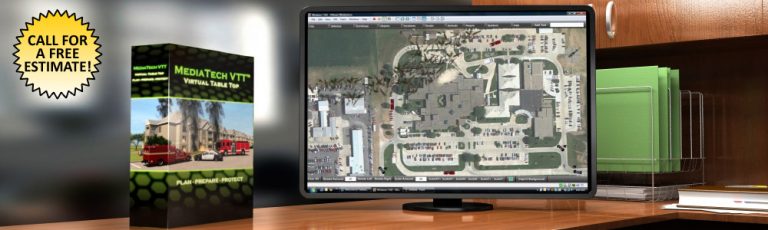
The Virtual Table Top – VTT™ is a web-based tool for conducting enhanced table top exercises. Facilitators and users can use custom backgrounds, place terrain features, roads, hazards, and equipment to visualize tactical and operational scenarios and response actions.
Exercise Support
MediaTech provides comprehensive expertise to support your emergency exercises, Workshops, Tabletops, Functional, and Full Scale, guiding you through every stage. We’ll assist with planning the exercise scenario, developing realistic simulations, and facilitating the event itself. Afterwards, we’ll lead a thorough evaluation and after-action review, pinpointing areas for improvement. We’ll then help you develop a concrete improvement plan and guide you through retesting the plan with the incorporated enhancements, ensuring your organization remains fully prepared for any emergency.
Why Use Split Encryption™ Products?
https://www.splitencryption.com/

To protect your data, we take your data then encrypt it with multiple encryption keys, then we split the transformed data and keys into multiple sections, and we distribute it to your server and our servers. Only a defined percent of your encrypted data and key will be distributed to your server and the remaining of the data will be stored on our data servers. We use a random encryption key for each record. The data NEVER store 100% of your data anywhere on our data warehouse or any full encryption keys on any servers. Nobody will be able to reconstruct your sensitive data without reconstructing all the data from multiple servers. By default, we only allow the IP(s) from your server to decrypt your data, only your server can decrypt your data, no hackers can decrypt it from any other IP addresses. Our products reach beyond HIPAA, PCI and GDPR compliance.
In summary, Split Encryption™ products offer a comprehensive, adaptive, and compliant solution to the multifaceted challenges of data security. By integrating our products into your security strategy, you can effectively protect your sensitive data from threats and ensure regulatory compliance.
Recent Projects

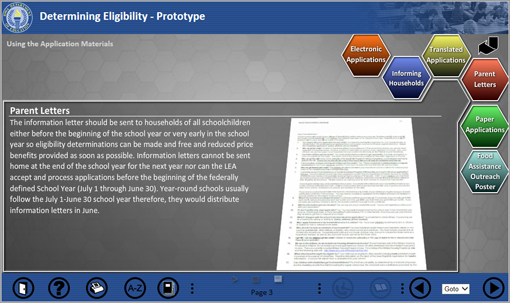
School Meal Programs Reference Library and Web-based Tutorial Development
At this time, Iowa does not have a comprehensive web-based resource for School Food Service personnel to access for guidance regarding the operation of a USDA School Meal Program. New Food Service Directors/Managers must navigate through several websites, manuals, and memoranda, all of which are not available in one central location. Currently, the Department offers a number of on-site and webinar training workshops around the state of Iowa to train new staff, update existing staff, and release guidance regarding new USDA School Meal Program regulations. These training opportunities are often not available on demand, and may only occur one time per school year. The comprehensive web-based reference library will provide a reliable resource, accessible at any time. In an effort to improve efficiency and efficacy of trainings, the Department seeks to develop web-based instructional tutorials. These tutorials will provide enhanced learning experiences, expanding upon reference library information. Additionally, the SA will have the ability to test comprehension and monitor completion as requirements for new Food Service Directors/Managers or as a component of Corrective Action.
HRF and CERFP for CERFP Basic Search and Extraction, and CERFP Collapse Specialist Course
MediaTech developed courseware selected from the HRF and CERFP for CERFP Basic Search and Extraction, and CERFP Collapse Specialist Course. HRF, CBRNE, CERFP lessons will employ advanced instructional strategies and interactive content to
establish a common frame of reference or platform to present information for NGB staff work that enhances the effective and efficient operation of the Joint Staff.
